Your cart is empty.

Stay Ahead of the Curve with Cyber Security Monitoring Services

Cyber security monitoring services are critical for businesses today. These services provide a way to detect and respond to threats in real-time, helping to protect your business from theft, vandalism, and other threats. Cyber security monitoring services are an important part of keeping businesses and individuals saf. Thus, Monarch is here to provide guidance on how to implement cyber security monitoring services and use them effectively.
Why You Need Cyber Security Monitoring Services

As a building owner, you are responsible for the safety of your employees and customers. A security breach can result in costly damages, legal liabilities, and a loss of business. Cyber security monitoring services can help you protect your property and business by deterring crime, detecting intrusions, and responding to emergencies.
Cyber security monitoring services provide 24/7 surveillance of your property. By enabling live professional monitoring, security personnel can monitor your building’s perimeter, entry points, and common areas. If an intrusion is detected, the security company will alert the appropriate parties.
In addition to deterring crime, cyber security monitoring services can also help you respond to fires, floods, or other emergencies. The security company will notify the authorities and provide them with real-time information about the situation. This can help minimize damage and prevent injuries.
Cyber Security Monitoring Services: Verkada’s Hybrid Cloud Architecture

Security monitoring in the cloud from Verkada combines the trustworthiness of local storage with the convenience of the cloud. Thus, neither NVRs nor DVRSs are required for Verkada’s cyber security monitoring services. Instead, up to a year’s worth of footage can be kept in Verkada’s solid-state memory. Of course, any data on the Command platform is also accessible remotely. Furthermore, Verkada’s hybrid cloud security monitoring tools are easy to scale and bandwidth-friendly. Due to Verkada’s design, businesses can deploy tens of thousands of security cameras in virtually limitless locations. Finally, Verkada boasts centralized management thanks to their state-of-the-art platform, Command, which provides users with safe, remote access to their data from any device, no matter where they happen to be located.
Consider the other important features of Verkada’s cyber security monitoring services:
User Friendly
- Verkada offers centralized management for streamlined vertical access to security devices anywhere
- There is no need for training to gain access to footage and features
- Locate, download, and share video from any device
- Regular, automatic software updates
Easy to Install
- No NVRs, DVRs, or servers are required, only a PoE connection
- In just a few minutes, cameras are online and ready to use
- There is no additional software or complication such as port forwarding

Scale-Ready
- Save on bandwidth as each camera only needs 20-50 Kbps in steady mode
- Expand to thousands of cameras in all locations
- No additional equipment is required to support additional cameras
No Hidden Fees
- Hardware comes with an industry-leading 10-year warranty
- System security is enhanced by automatic firmware updates
- No extra charges for the addition of new features and enhancements
What Are the Advantages of Cyber Security Monitoring Services?

There are many benefits to employing cyber security monitoring services in your organization’s surveillance system. While more benefits will be discussed in later sections, here is an overview of the advantages of cyber security monitoring services with cloud-based devices:
- Secure remote access from nearly anywhere on any device
- Real-time alerts if cameras go down
- SAML-based integration with single-sign on (SSO) solutions
- Continuous upgrades with new AI functions
- Quickly share live footage via SMS and email
- Live, preemptive alerting based on suspicious behaviour
Cyber Security Monitoring Services: Command Platform Overview
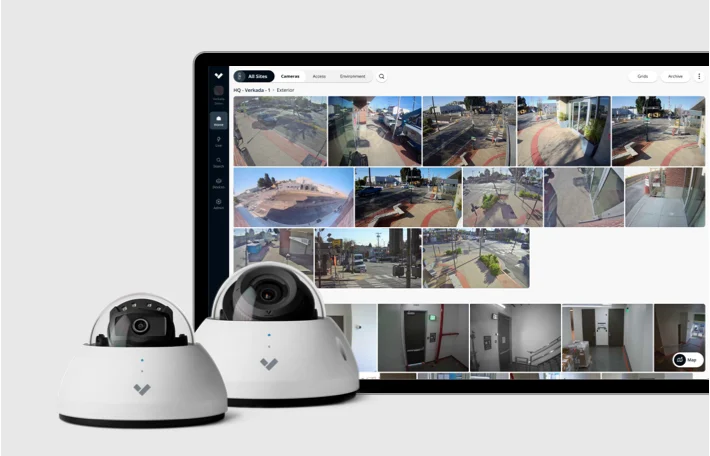
Verkada provides a cloud-based management software for all Verkada security devices. Verkada’s cloud-based management software, Command, provides straightforward access and management of all cameras and users across all sites, from virtually anywhere in the world. From the Command interface, users can configure new cameras, create new sites, manage settings, access live and archived footage, manage users, and gain access to advanced features powered by Verkada’s edge-based analytics. Verkada’s Command platform boasts a number of features including, but not limited to, the following:
Permissions & Security
- Support for SAML/OAuth for single sign-on
- Options for two-factor authentication
- User permissions can be set at the camera, site, and organizational levels.
Remote Control
- Access from nearly any device (desktops, smartphones, tablets)
- Native apps for iOS, Android, and Verkada’s VX52 Viewing Station
Share and/or Archive
- Command licenses entail virtually limitless cloud archiving
- Quickly export any recordings in a shareable MP4 format
- Create and send Live Links to emergency personnel
Edge–Based Analytics
- Search footage by a number of factors including time of day, data, and motion
- Simplify investigations with People and Vehicle Analytics
Scalable
- Unlimited storage on camera and cloud
- Authorize admins access to an unlimited number of users.
- Infinitely scalable, no matter how large the facilities are
Verkada for Cyber Security Monitoring Services
At Monarch, we will collaborate with you to develop the most suitable security system with cyber security monitoring services for your organization. We’ll work together to create, implement, and manage a cloud-based security system that prioritizes both protection and comfort.
Verkada offers a wide range of cloud security monitoring devices, including cameras, access control, environmental sensors, and visitor management. All Verkada devices integrate with each other and are managed from a single cloud dashboard.
Cyber Security Monitoring Services: Benefits of Verkada Cloud-Based Cameras

Verkada offers technology that is secure and easy to use for users looking for reliable security. The set-up is simple: once a device is installed, it is online and fully operational within just a few minutes.
Other features and services of our security cameras include the following:
- AI-Based Video Analytics: Face detection and person of interest detection. You can easily receive alerts when a person of interest re-enters your business.
- Smart Filters: Search for specific people, vehicles, and objects without having to spend too much time scrubbing through footage.
- License Plate Recognition: Identify license plates of interest in your parking lot.
- Shareable Live Feeds: Share your live feed via SMS. This is useful as you can send it to first responders in case of an emergency for dramatically reduced response time.
- Time lapse: Watch a day of footage in under 30 seconds with timelapses.
- Floor Plan: Quickly respond to incidents with real-time motion plotting.
Additionally, Verkada offers security cameras that are thoughtfully designed. The cameras have a durable design, firmware signing, and can detect tampering. Choose the security cameras that fit your needs and ensure safety.
Cyber Security Monitoring Services: Verkada’s Cameras for Security
We offer a variety of options to meet your security monitoring needs including: the Verkada Indoor Dome Series, the Verkada Outdoor Dome Series, the Verkada Bullet Series, the Verkada Mini Series, and Verkada Fisheye Series.
Verkada Indoor Dome Series

The Verkada Indoor Dome Camera is designed for indoor, high-traffic areas. It is the perfect general-purpose security camera if you’re looking to expand your security system with cloud security monitoring services. There are three versions of this camera: CD42, CD52, and C62.
| CD42 | CD52 | CD62 | |
| Type | Indoors | Indoors | Indoors |
| Image Resolution | 5MP | 5MP | 4K |
| Type of Lens | Fixed, with 3x Zoom Digitally | Zoom, with 3x Optical and Digital Zoom | Zoom, with 3x Optical and Digital Zoom |
| Standard Retention | Up to 365 Days | Up to 365 Days | Up to 90 Days |
| Standard Storage | Up to 2TB | Up to 2TB | Up to 2TB |
| Audio | Yes | Yes | Yes |
| IR Range | 15m | 30m | 30m |
| Rating | IK08 | IK08 | IK08 |
The Verkada Outdoor Dome Series

The Verkada Outdoor Dome Series is both weather- and tamper-resistant. Its capabilities function well even in areas with limited bandwidth and connectivity. They are perfect for monitoring the parking lot and the exterior of buildings (e.g., to capture key license plates). There are three versions of this camera: CD42-E, CD52-E, and C62-E.
| CD42-E | CD52-E | CD62-E | |
| Type | Outdoors | Outdoors | Outdoors |
| Image Resolution | 5MP | 5MP | 4K |
| Type of Lens | Fixed, with 3x Zoom Digitally | Zoom, with 3x Optical and Digital Zoom | Zoom, with 3x Optical and Digital Zoom |
| Standard Retention | Up to 365 Days | Up to 365 Days | Up to 90 Days |
| Standard Storage | Up to 2TB | Up to 2TB | Up to 2TB |
| Audio | Yes | Yes | Yes |
| IR Range | 15m | 30m | 30m |
| Rating | IK10 & IP67 | IK10 & IP67 | IK10 & IP67 |
The Verkada Bullet Series

The Verkada Bullet Series is ideal for long range, outdoor surveillance. It is built to withstand harsh environments, making it a durable cyber security monitoring tool. The Verkada Bullet camera is available in two lens types: wide angle and telephoto. There are four versions of this camera: CB51-E, CB61-E, CB51-TE, CB61-TE.
| CB51-E | CB51-TE | CB61-E | CB61-TE | |
| Type | Indoor and/or Outdoor | Indoor and/or Outdoor | Indoor and/or Outdoor | Indoor and/or Outdoor |
| Image Resolution | 5MP | 5MP | 4K | 4K |
| Type of Lens | Zoom, with up to 3x Optical and Digital zoom | Telephoto Zoom, with 8-20mm focal length | Zoom, with up to 3x Optical and Digital zoom | Telephoto Zoom, with 8-20mm focal length |
| Standard Retention | Up to 2TB | Up to 2TB | Up to 2TB | Up to 2TB |
| Standard Storage | Up to 365 Days | Up to 365 Days | Up to 90 Days | Up to 90 Days |
| Audio | – | – | – | – |
| IR Range | 30m | 50m | 30m | 50m |
| Rating | IK10 & IP167 | IK10 & IP167 | IK10 & IP167 | IK10 & IP167 |
The Verkada Mini Series

The Verkada Mini Series offers both flexibility and enhanced resolution for clear footage. The Mini Camera is a compact size that can fit any space, anywhere indoors. There are three versions of this camera: CM41-S, CM41, and CM41-E.
| CM41-S | CM41 | CM41-E | |
| Type | Indoor | Indoor | Outdoor |
| Image Resolution | 5MP | 5MP | 5MP |
| Type of Lens | Fixed, with up to 3x Digital Zoom | Fixed, with up to 3x Digital Zoom | Fixed, with up to 3x Digital Zoom |
| Standard Retention | Up to 90 days | Up to 365 Days | Up to 365 Days |
| Standard Storage | Up to 385GB | Up to 2TB | Up to 2TB |
| Audio | – | Yes | – |
| IR Range | N/A | 15m | 15m |
| Rating | N/A | IK08 | IK10 & IP67 |
The Verkada Fisheye Camera

The Verkada Fisheye Camera provides a panoramic view of the entire property – both indoor and outdoor. This camera allows for total surveillance coverage, making it an ideal cyber security monitoring device.
| Fisheye CF81-E | |
| Type | Indoor and/or Outdoor |
| Image Resolution | 12MP |
| Type of Lens | Fixed, with 3x Digital Zoom |
| Standard Retention | Maximum of 90 Days of Standard Quality Retention |
| Standard Storage | Up to 2TB of Onboard Storage |
| IR Range | 20M |
| Angle of View | 180° |
| Rating | IK10 and IP67 |
| Audio | Yes |
| NDAA Compliant | Yes |
| Analytics | Ambarella Chipset for People and Vehicle Analytics |
| Viewing Modes | Panoramic; Four–Way Split; Pan-Tilt–Zoom |
The Verkada Fisheye Camera (CF81-E) is an ideal security camera. With the option to switch between circle, ePTZ, 2-view, 3-view, or 4-view modes on the CF81-E, you can do away with the need for multiple camera installations. You can also take advantage of features like digital pan-tilt-zoom to increase coverage and lessen blind spots.
Three different view modes are supported by the CF81-E. You can customize the view mode to meet the requirements of the install location.
- 180° Panoramic: A wide-angle view that is ideal for an open area or a corridor.
- Four-way split: Use a single camera to watch four distinct fields of view.
- Pan-tilt-zoom (ePTZ): Provides a panoramic, all-encompassing view of your environment.
Panoramic

Panoramic is the first view mode of the fisheye camera. The camera will have a 180° horizontal field of view in this mode. The camera can be tilted to adjust the fields of view to your preferences.
Four-Way Split

Four-Way Split is the second mode of the fisheye camera. You can monitor four distinct areas all at the same time using the Four-Way Split mode. It’s especially useful for monitoring an outdoor corner, a hallway intersection, or when replacing multiple cameras with one. Site administrators can adjust the Four-Way Split’s angles to better suit their needs and maximize the fields of view.
Pan-Tilt-Zoom (PTZ)

Pan-Tilt-Zoom (PTZ) is the third, adaptable mode of the fisheye camera. You can choose to display the video feed in Pan-Tilt-Zoom as a 360° view, a tiles view with various angles, or by using your digital PTZ functionality to pan, tilt, and zoom around the image.
| 180° Panoramic | Four-way Split | Pan-Tilt-Zoom | |
| Privacy Zones | Y | Y | Y |
| People Counting | Y | Y | – |
| People Analytics | Y | Y | – |
| Vehicle Counting | Y | Y | – |
| Vehicle Analytics | Y | Y | – |
| Crowd Alerts | Y | Y | – |
| Motion Alerts | Y | Y | Y |
| Motion Search | Y | Y | Y |
| Audio | Y | Y | Y |
Continuous Cyber Security Monitoring

Remote security is a cyber security monitoring service that allows security professionals to keep an eye on your property and assets from afar 24 hours a day, seven days a week. There are many benefits of having remote security monitoring as part of your security tool set. Some benefits includes deterring crime, catching criminals in the act, providing evidence for criminal prosecution, and peace of mind.
- Deter Theft, Vandalism, and Crime: Security systems with remote security monitoring can be an effective deterrent to criminals. If potential criminals are aware that their activities are being actively monitored, their likelihood of committing a crime decreases.
- Identify Criminals in Real-time: Remote security monitoring is an important security measure as it can help catch criminals in the act. This type of system provides a proactive approach to security by alerting security personnel to potential risks as they are happening, rather than after the fact.
- Provide Evidence: Remote security monitoring can also provide evidence for prosecution in the event of a crime. This ensures that criminals are apprehended and prosecuted, and it may protect your building from a repeat offense.
- Peace of Mind: Remote security monitoring can provide peace of mind for business owners. Knowing that your property has round-the-clock protection in the event of an emergency can help reduce anxiety and stress levels.
Cyber Security Monitoring Services: Access Control

Another critical security service is access control. An access control system is a security measure that regulates who has access to certain premises. There are many different types of access control systems, but they all have one common goal: to keep unauthorized people out while allowing authorized people in. Furthermore, access control allows staff to move around quickly with keycards to maximize efficiency.
There are numerous approaches to controlling access to a building, and Monarch can assist you in determining which approaches to use for your security system.
Cyber Security Monitoring Services: Verkada’s AC41 Door Controller

With Verkada’s AC41 Door Controller, clients may bring plug-and-play ease to managing doors and access throughout their buildings. In other words, as soon as you install the AC41 Door Controller, it is ready to use within minutes! Our Access Controller can easily integrate with any existing door hardware and readers in your facility.
With our Command platform, you can easily manage your doors once they are connected to the network (e.g., create lock schedules for doors). On the Command platform, you can effortlessly manage building access, scheduling, and users. You also save time adding users on the platform since employees are seamlessly configured, onboarded, and offboarded. This is because of the integration with active directory platforms.
Additionally, you can easily connect your Access Controller with your cameras using Verkada Command to provide real-time video analytics on access-related events. Thus, you are able to not only view what is happening at the buildings’ points of entry, but also take proactive action for any significant occurrences.
Cyber Security Monitoring Services: Verkada’s AD32 Door Reader

The AD32 Door Reader allows individuals to enter doors if they have the appropriate credentials on their cards or mobile phone. This door reader supports low and high frequency card formats as well as mobile devices that have the Verkada Pass app. Furthermore, the AD32 Door Reader comes in two different options: the Mullion Mount Plate and the Single Gang Mount Plate. Both options allow for customized installs.
The Single Gang Mount Plate is a common card reader format that can replace existing reader mounts or be used on traditional installations. The thinner Mullion form factor has a sleek design and can be used in smaller spaces such as door frames.
Access Control Key Features

With Verkada, choosing the right security services is made easy. Consider the following key features of Verkada’s access control:
- Seamless Video Integration and Analytics
- Infinite Scalability
- Cloud-Based Software and Management
- Integrate the Access Controller with Any Existing Cards and Readers
- 10-year Warranty on Hardware
- Verkada’s Pass App: Touchless Access Capability with Bluetooth
The Uses of Access Control
You can feel secure knowing that your interests are safeguarded with any Verkada device. Consider the following benefits of implementing access control as part of your security plan:
Insight on Building Access Activity
- Our access control system handles visitor credentials and ensures that visitors like maintenance workers only have access to specific areas.
- Track where and when individuals enter and exit certain areas.
Intrusion Detection
- Deter deter potential crime with safety door locks after business hours.
- Identify intrusions when they do occur. With Verkada’s devices, you can filter for door events like tailgating, holding the door open, forcing the door open, and people of interest.
Asset Protection
- Prevent some employees and visitors from entering restricted areas with door lock systems that require authorized credentials.
- Protect your company’s critical equipment, information, and assets with controlled access door locks. With these door locks, only authorized individuals will have access to these areas.
Managing Access Credentials
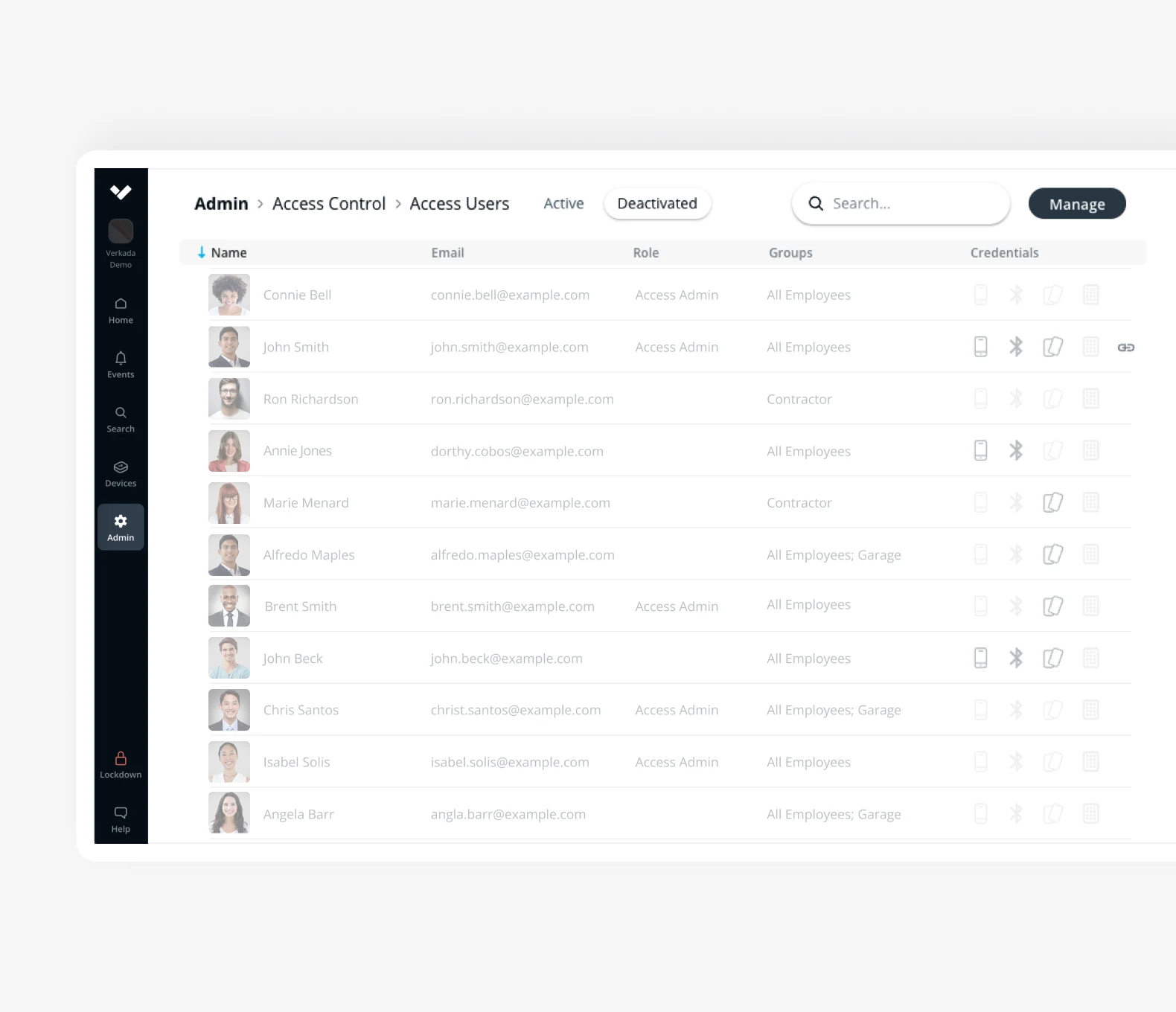
So, how does Verkada’s access control work? You can manage access control on the Verkada Command platform which is where you can monitor all of your devices. There are many different features that you may use to secure access control.
First, you can specify the user groups or access levels on Verkada Command. Then, you can design badge templates for each user group or access level. Next, you can print the badges and issue credentials either in bulk or individually. Finally, you can maintain users and permissions up to date in real time.
What else can be done on Verkada Command to manage building access control? Consider the following features:
- Synchronize Profiles: Synchronize users from SSO systems such as Okta and Azure Active Directory, and natively capture access levels and groups.
- Provisioning with a Single Click: With a single click, employees can be issued bluetooth credentials or a physical ID card.
- Log of Badge Events: On Verkada Command, access a log of badge events to ensure that only authorized individuals have access to secure areas.
- Secure De-provisioning: Instantly and automatically deprovision users from all systems and access points.
- Unlock Doors from Anywhere, Anytime: Users can remotely unlock authorized doors using either the Verkada Pass and Command Mobile apps
- One-Tap Instant Lockdown: Create custom Lockdown scenarios that can be activated with a single tap to immediately secure buildings in the event of an emergency.
Cyber Security Monitoring Services: The SV11 Environmental Sensor

The Verkada SV11 all-in-one environmental sensor can monitor the health and safety of buildings, taking security to a whole other level. The SV11 environmental sensor monitors 8 different aspects of the environment: the total volatile organic compounds (TVOCS), the air quality index (AQI), particulate matter 2.5 (PM 2.5), the temperature and relative humidity, noise levels, vaping, and motion. Overall, the automated situational awareness provided by the SV11 is key in improving safety and security.
Verkada’s SV11 is an essential cloud security tool. The cloud-based sensor instantly connects to the cloud via Ethernet. This makes it easy to scale since there are no servers, databases, or on prem clients to manage. Moreover, since they are cloud-based, sensors are ready to use within minutes. You can then manage the sensors from Verkada’s web-based Command platform. This makes it easy and secure to remotely access on any device, anywhere. Furthermore, sensor security is maintained through continual, automatic firmware updates.
You can purchase the SV11 Environmental Sensor here.
Design and Features of the SV11

The SV11 is unique in not only its ability to monitor the overall environment, but also in its design and features, making it the perfect addition to your cloud security toolkit. Its outer layer is a photochemically stainless steel etch and it is followed by several different sensors that measure and report data. Verkada’s SV11 works by using the onboard sensors to detect changes in the breakdown of chemicals in the air.
Furthermore, the SV11 has many different features that make it one of the most appealing environmental sensors. Consider the following unique attributes:
- Command Platform: Access all sensor data from the Command platform and view it against a timeline to get a full picture of when these events occurred. Compare environmental between any number of sensors or locations.
- Customize Your Dashboard: Determine which exact sensor data you’d like monitored and displayed on your dashboard
- Easy Visualization of Data: Data is easily visualized with color-coded sensor readings and data representations.
- Integration with other Verkada Devices: The SV11 Environmental Sensor is natively integrated with all other Verkada devices.
- Link Sensor-Based Data to Video: Link any sensor with a Verkada camera, correlating video with sensor-based data.
- Custom Threshold: Configure custom alert thresholds to receive real-time notifications via SMS and email.
- Sensor-Based Alerts: When an anomaly is detected, an alert via SMS or email can be sent to pre-selected individuals as well as security, allowing teams to respond quickly.
- Alert Settings: Customize alerts for your team to cut down on unnecessary notifications during the weekend and after work. Our platform allows each user to set what hours and days of the week that they’d like to receive alerts for sensor-based anomalies.
The Benefits of The SV11 Environmental Sensor

Consider the following advantages of having the SV11 sensor as part of your security system:
Detect Dangerous Environmental Conditions
- Deter harmful behaviors like vaping
- Monitor changes in temperature or humidity to reduce the loss of records or products
- Measure the air quality to ensure healthy air quality for employees and for product control
- Measure VOC emissions to prevent adverse health effects
Remain Safe and Secure
- Monitor the environment to ensure measurements are in line with state laws and compliances.
- Monitor noise levels that may indicate yelling is happening. This can help different institutions monitor for violence, conflicts, or other issues.
- Monitor the temperature to protect expensive equipment and products.
Maintain Privacy
- Monitor noise levels without recording audio. This ensures privacy is not compromised
Choosing Verkada for Cyber Security Monitoring Services
Cloud security monitoring are necessary in order to maintain a safe and secure environment for employees, customers, students, and/or visitors. At Monarch, we’re here to help you choose the best security tools.
Explore Verkada Updated: Nov 15














 Jon Jones
Jon Jones