Your cart is empty.

Maximize Security with State-of-the-Art Perimeter Protection Systems
Secure Your Property with Cutting-Edge Perimeter Security Solutions
At Monarch, we understand the critical importance of perimeter security in safeguarding your premises. Our range of advanced perimeter security solutions with Verkada products are designed to provide robust protection against potential threats.
From intelligent surveillance systems to access control technologies, our team of security experts is ready to assist you in implementing the most effective solutions for your specific needs. Connect with us today to explore the possibilities and enhance your perimeter security measures.
What to Look for in Perimeter Security Solutions
When considering perimeter security solutions for your property, it is important to choose the right features that align with your security needs. Here are three key aspects to look for when evaluating perimeter security solutions:

Comprehensive Surveillance
Opt for solutions that provide robust surveillance capabilities, including high-resolution cameras, wide coverage angles, and low-light visibility. This enables effective monitoring and recording of the perimeter.

Intrusion Detection
Look for systems equipped with advanced intrusion detection features such as motion sensors. These features can detect and alert you of any unauthorized entry attempts or suspicious activities along the perimeter.

Access Control Integration
Consider perimeter security solutions that seamlessly integrate with access control systems. This allows you to manage and control entry points, gates, and barriers. You can also grant access only to authorized individuals.
Benefits of Perimeter Security Solutions
Effective perimeter security solutions play a vital role in protecting your premises from potential threats and unauthorized access. By implementing these solutions, you can enjoy a range of benefits that enhance your overall security posture.
- Enhanced Deterrence: Visible security measures act as a deterrent, discouraging potential intruders from targeting your property.
- Early Detection: Advanced surveillance systems and sensors provide early detection of suspicious activities, allowing for timely response and intervention.
- Quick Response: With real-time monitoring and alerts, security personnel can swiftly respond to any security breaches or emergencies.
- Reduced Risks and Losses: By preventing unauthorized access and detecting threats early on, you can minimize the risk of theft, vandalism, or other security incidents.
- Insurance Benefits: Implementing robust security measures may lead to reduced insurance premiums as it demonstrates a proactive approach to risk management.
Why Choose Verkada?
Verkada solutions stand out from traditional security systems because they are designed to be user-friendly, scalable, and flexible all while providing enterprise-grade security.
User-Friendly
- Solid-state Storage (SSD): No NVR, DVR, or server needed!
- Simple Plug-and-Play Install: Only a Ethernet cable is required for cables to be brought online and fully operational within minutes
- Regular, Automatic Software Updates: Reduces extra overhead operations
- Time lapse: No need to waste time on scrubbing through footage!
- Floor Plan: Gain a comprehensive understanding of what is occurring throughout your facility
- Remote Access 24/7: From anywhere with an Internet connection, at any time, with any device
Limitlessly Smart
- AI-Based Video Analytics: Face detection, license plate detection, and more!
- Smart Filters
- Live Alerts: Receive alerts in meaningful incidents.
- Shareable Live Feeds: Share via SMS to first responders and others.
- 10-Year Warranty
Scalable
- Unlimited Storage on Camera and Cloud: Unlimited archiving with Verkada’s cameras
- Unlimited Users Allowed: Easily authorize admins access to any number of users
- Infinitely Scalable
Verkada Security Cameras for Perimeter Security Solutions
Upgrade your perimeter security with Verkada’s advanced security cameras, available at Monarch. These cutting-edge cameras are designed to provide robust surveillance and protection for your property.
With features like high-resolution imaging, intelligent analytics, and seamless integration, Verkada cameras offer unparalleled visibility and detection capabilities. Monitor your perimeter in real-time, deter potential threats, and ensure the safety of your premises with Verkada’s reliable and innovative security cameras. Enhance your perimeter security solution today.
The Dome Series for Perimeter Security Solutions
The Dome Series from Verkada provides enterprise-grade security in a variety of models suitable for any environment – indoors or outdoors. These IP security cameras have a long-lasting, vandal-resistant design and sensor resolutions of up to 4K. They are the ideal, general surveillance camera for perimeter security solutions.
Design
- Durable, vandal-proof housing with outdoor models having a weather-resistant design
- Indoor models: IK08 impact rating
- Outdoor models: IK10 impact and IP67 weather ratings
Functionality and Storage
- High resolution cameras — 5MP or 4k
- 4k available only on CD62 & CD62-E
- Max of 365 days of footage storage in standard quality
- 128GB – 2TB of onboard storage
- Equipped with audio
- Low–bandwidth impact
Features
- Edge processing for motion, People, and Vehicle Analytics
- Occupancy Trends available only on Dome Series cameras
- Zoom capabilities – both optical and digitally
- CD42, CD42-E: Fixed, with 3x Zoom Digitally
- Other models: Zoom, with 3x Optical and Digital Zoom
- IR Range
- 15m (CD42, CD42-E)
- 30m (CD52, CD52-E, CD62, CD62-E)
The Bullet Series for Perimeter Security Solutions
The Bullet Series from Verkada is built to withstand extreme conditions, and its conspicuous appearance is meant to deter would-be assailants. Essentially, it is the ideal cloud-based security camera solution for harsher environments.
Design
- Durable and weather-proof camera for perimeter security solutions
- IP67 weather rating and IK10 impact rating
- Lens – Choose between wide-angle or telephoto
Functionality and Storage
- High resolution cameras – up to 4k
- 4k available only with CB62-E and CB62-TE
- Max of 365 days of footage retention in standard quality
- 265GB–2TB of onboard storage
- Low–bandwidth impact
Features
- License Plate Recognition available only for telephoto cameras
- Edge-based processing for motion, people and vehicle analytics
- NDAA compliant
- Zoom capabilities
- CB52-E, CB62-E: Zoom, with up to 3x Optical and Digital zoom
- CB52-TE, CB62-TE: Telephoto Zoom, with 8-20mm focal length
- IR Range
- CB52-E, CB62-E: 30M
- CB52-TE, CB62-TE: 50M
The Mini Series for Perimeter Security Solution
Verkada’s mini series offers a compact and discreet security solution for perimeters. These cameras are designed to be small and unobtrusive, making them well-suited for installation in tight spaces or in areas where a larger camera may be noticeable.
Design
- Small and discreet camera with 5MP resolution
Functionality and Storage
- Max of 365 days of footage retention in standard quality
- 128GB – 2TB of onboard storage
- Low band-width impact
Features
- Edge–based processing for motion and tamper detection along with People Analytics
- Fixed, with up to 3x Digital Zoom
- Audio available only on CM41 and CM41-E
- IR Range: 15m for CM41 and CM41-E
- N/A for CM41-S
The Fisheye Series for Perimeter Security Solutions
Verkada’s fisheye cloud-based security camera offers dynamic viewing experiences with sophisticated onboard processing and a wide–angle 12MP image sensor.
In fact, there are five different viewing options available to users: panoramic, digital pan-tilt-zoom, 2-way split, 3-way split, and 4-way split. This makes it an ideal perimeter security solution for businesses seeking to reduce the number of cameras they need.
Design
- Durable and weatherproof
- IP67 weather rating and IK10 impact rating
- 12MP image sensor for wide–angle coverage
Functionality and Storage
- Max of 90 days of footage retention in standard quality
- 512GB–2TB of onboard storage
- Low–bandwidth impact
- 180 degree field of view
Features
- Five viewing modes
- Nighttime visibility with IR illuminators (20m/66ft)
- NDAA
- Equipped with audio
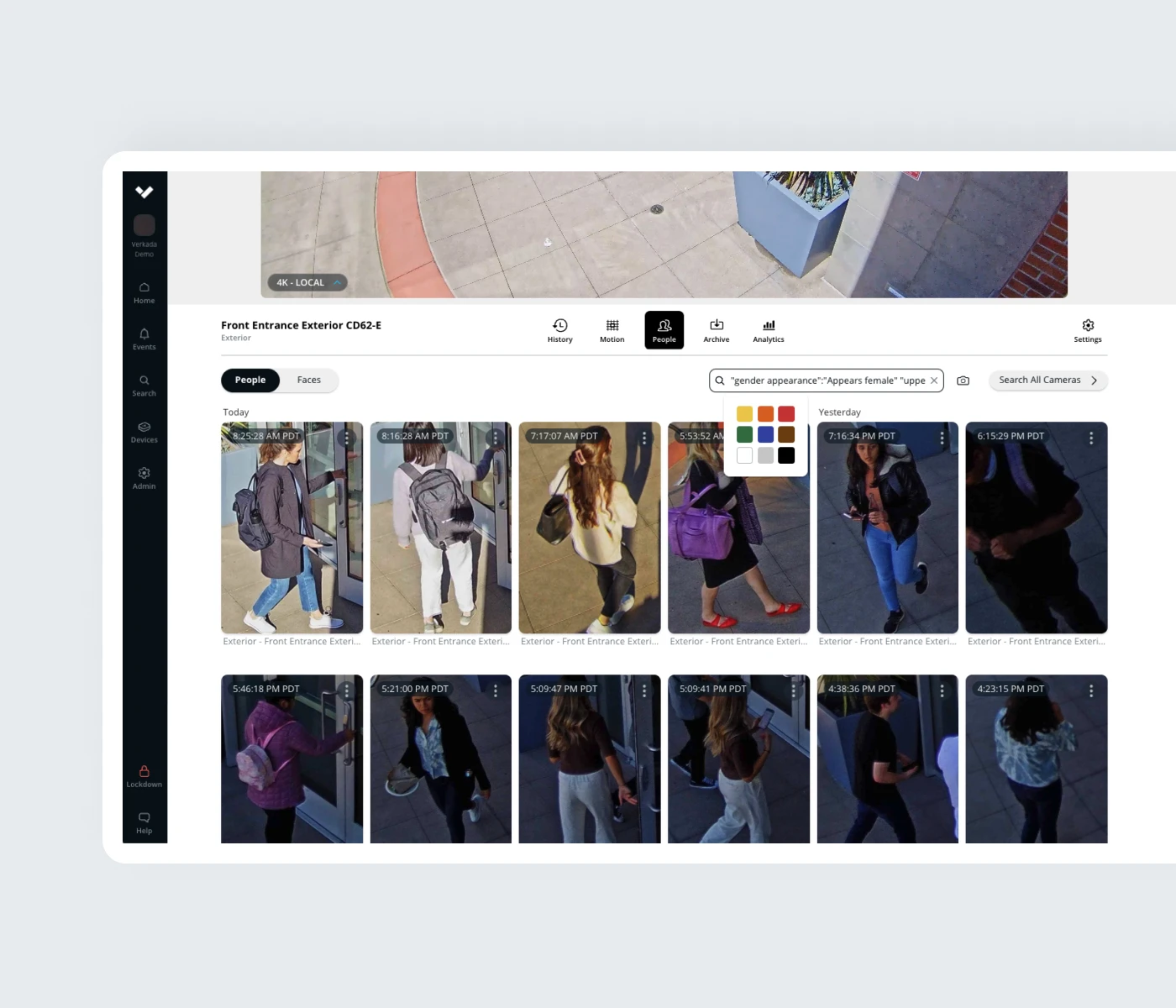
People Analytics
People Analytics combines cloud-based computer vision with intelligent edge-based video processing to give users high-quality images of every person recognized in the scene. This enables Facial Recognition capabilities – an ideal perimeter security solution for businesses with many people coming and going.
- Face Search*
- You can quickly find people who look like a face you already have in your enterprise. You can also upload an image of a face of a person of interest.
- Occupancy Trends
- Estimate the number of people who cross a customizable digital line on a video feed.
- Keep track of how a space is being used in order to improve business operations.
- Person History
- Search through high-resolution snapshots of people detected in the frame.
- Save screenshots or easily access associated high-resolution video.
- Examine Anywhere
- People Analytics is accessible from any device and from virtually any location in the world.
- Filters for Attributes
- Filter by a variety of criteria, such as clothing color, gender appearance, and facial matches.
- Cross Camera Tracking
- Quickly identify people of interest or potential suspects across all cameras at all sites.
- Record and export multiple angles of a person to provide evidence quickly.
*It is important to use the face recognition technology ethically, respecting individuals’ rights to privacy and avoiding bias.
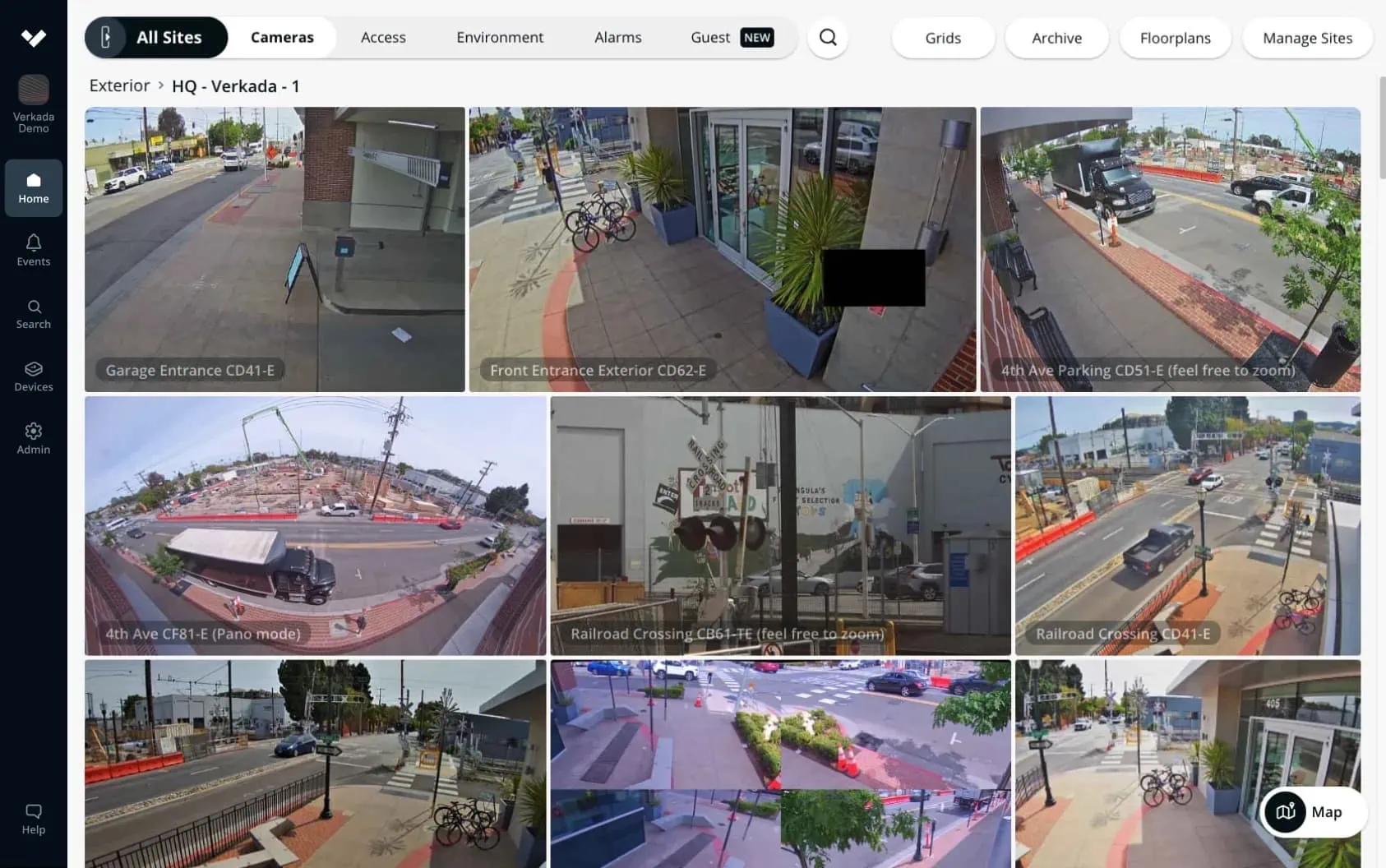
Remote Security Monitoring
Remote security monitoring is a process that allows security professionals to keep an eye on your building’s perimeter from afar 24 hours a day, seven days a week.
Step 1: Choose the Cameras for Site Surveillance
You begin by determining which cameras will be watched and at what times. Verkada’s high-tech AI analytics then notify on-call security personnel whenever a human is detected at the scene.
Step 2: Security Officer Checks for Danger
Second, when an alarm goes off, the people who are watching the live video feed will look at the footage to see if anything is in immediate danger.
Step 3: Security Officer Responds to Incidents
Ultimately, if there is a real danger, the monitoring agent will immediately contact the customer’s call list. In the event of an emergency, customers can also request that agents contact the appropriate authorities.
VX52 Viewing Station
The Verkada VX52 Viewing Station is a dedicated video wall solution that streams up to 300 camera feeds with ultra-low latency, crisp video playback, customizable layouts, and Smart Tiles. It is an ideal security solution for large businesses seeking to surveil their buildings’ perimeters.
- Plug-and-play device with zero local configuration required
- Customizable Smart Tiles to prioritize events like high-motion activity, door access control, and environmental sensor data
- Administrator-managed device with no need for additional accounts
- Backed by a 10-year warranty
Warranty
All Verkada hardware has a 10 year warranty from the date of shipment. For more information, click here.
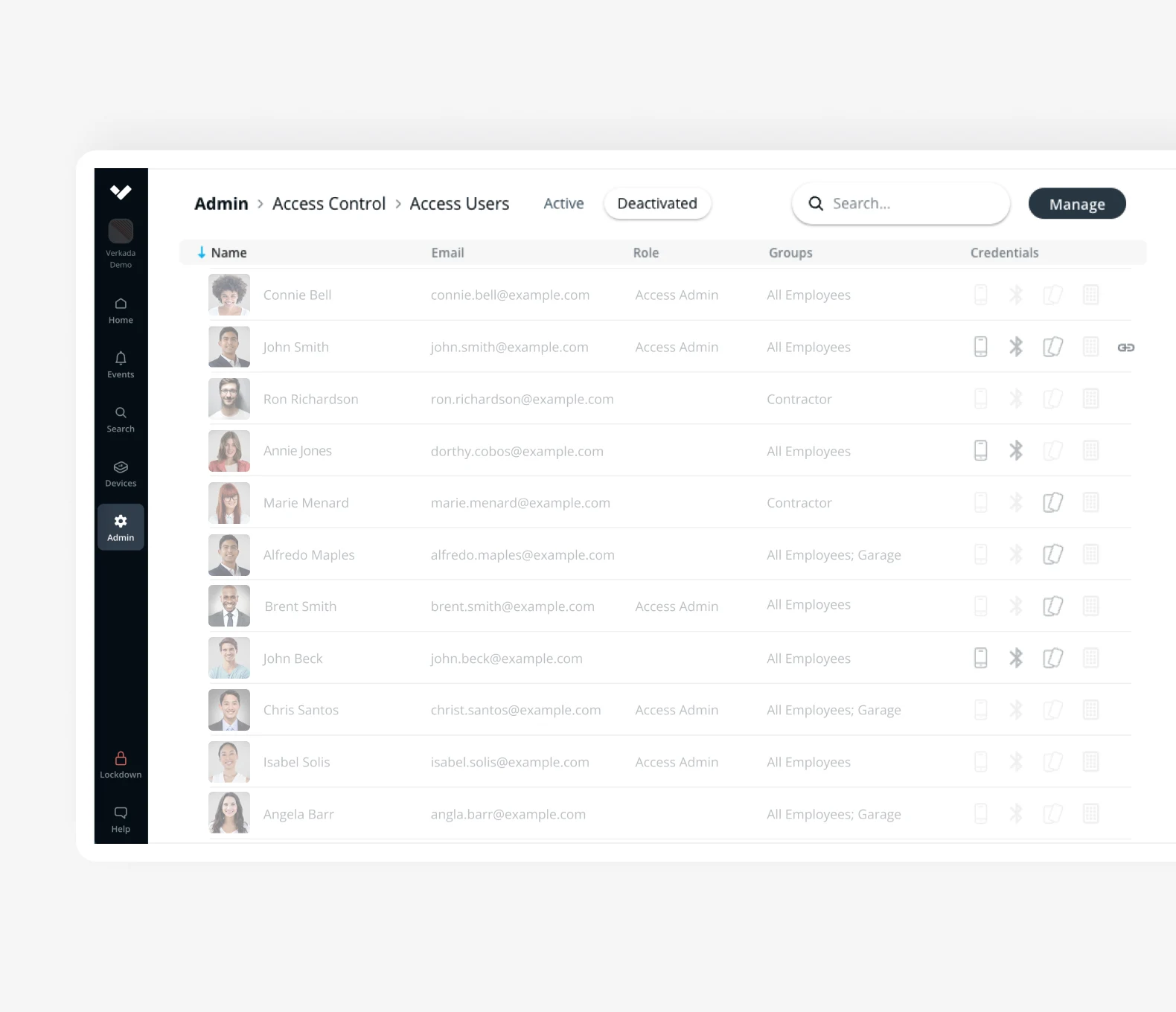
Verkada Access Control for Perimeter Security Solution
Verkada’s access control systems offer a robust perimeter security solution designed to enhance the safety and security of enterprises.
These access control systems offer advanced features such as keyless entry, remote management, and real-time activity tracking, providing a secure and efficient monitoring solution for your remote security needs.

Door Controller AC41
Priced at $1799

AD32 Multi Format Card Reader
Priced at $349

AX11 IO Controller
Starting at $216.50 per month
The Verkada AC41 Door Controller
This door controller is a powerful and easy-to-use perimeter security solution that combines enterprise-grade security with a cloud-based management platform.
- Easily manage doors and access across your organization on the Command platform (schedules, users, building access)
- Connect with Verkada’s video security system for real-time video analytics on access events
- Supports secure touchless access using Bluetooth and Verkada’s Pass app
- Works with existing door hardware and readers
- Seamless integration to active directory platforms for automatic employee configuration, onboarding, and offboarding.
- 10-year warranty on all hardware

The Verkada AD32 Door Reader
This Verkada door reader is a versatile and robust access control device that allows individuals to enter doors using low and high-frequency cards or a mobile device with the Verkada Pass app. Consider the following attributes of the Door Reader that make it an ideal perimeter security solution:
- Can withstand a harsh environment – IP65 and IK08 ratings
- Controlled through the Command platform
- Two different options:
- Mullion Mount Plate: This option has a sleek design and can be used in smaller spaces such as door frames.
- Single Gang Mount Plate: This is a common card reader format that can replace existing reader mounts or be used on traditional installations.

The Verkada AC62 16 Door Controller
The AC62 16 Door Controller is an enterprise-grade access control panel that simplifies access control for up to 16 doors. It offers the scale and simplicity of the cloud, making access control more efficient and effective with native cloud-based access control. Easily scale your enterprise’s access control with this perimeter security solution!
Enhanced Security Features
- Seamless integration with Verkada or third-party readers, REX devices, AUX inputs, and wet or dry lock configurations.
- Connection to the Fire Alarm Interface for emergency events.
- Customizable access levels and schedules, allowing for tailored access control based on employee roles and schedules.
- Ethernet connection to Verkada Command eliminates the need for servers and thick or thin clients.
- Easy-to-use wiring terminals for simplified installation.

The Verkada AX11 IO Controller
The AX11 IO Controller from Verkada is a versatile and scalable device that enables enterprises to integrate more inputs and outputs to their existing access control systems. With 16 inputs and 16 outputs, users can easily integrate access control, cameras, sensors, and alarms.
Simple, Scalable, and Flexible Perimeter Security Solution
- Seamless integration with Verkada cameras: The AX11 IO controller enables easy monitoring and tagging of video events for door-based events, intrusion detection, and more
- Event Bridge technology: This feature allows you to bring door events with video analytics into the Command platform while using your existing access control or alarm system. Also provides real-time alerts and reports
- Supports third-party card door readers: The AX11 IO controller works with Verkada and third-party card door readers, offering you the flexibility to choose the best access control solution for your business.
- Elevator access control:Manage access to different floors of your building with a Verkada or Wiegand reader.
- Simplified installation: The AX11 IO controller comes with removable connectors and cable management loops, making wiring simple and streamlined.

Access Control: How it Works
You can manage your enterprise’s access control solutions on the Verkada Command platform which is where you can monitor all of your devices.
- Specify the user groups or access levels of the facility on Verkada Command.
- Design badge templates for each user group or access level
- Print the badges and issue credentials either in bulk or individually
Command Features
- Synchronize Profiles: Synchronize users from SSO systems such as Okta and Azure Active Directory, and natively capture access levels and groups.
- Provisioning with a Single Click: With a single click, employees or students can be issued bluetooth credentials or a physical ID card.
- Log of Badge Events: On Verkada Command, access a log of badge events to ensure that only authorized individuals have access to secure areas.
- Unlock Doors from Anywhere, Anytime: Users can remotely unlock authorized doors using either the Verkada Pass and Command Mobile apps
- One-Tap Instant Lockdown: Create custom Lockdown scenarios that can be activated with a single tap to immediately secure buildings in the event of an emergency.
The SV20 Environmental Monitoring Series
The SV20 Series by Verkada is a line of robust air quality sensors designed to meet a variety of environmental monitoring needs. The series consists of three models, each with different capabilities to detect and monitor air quality.
The SV21 is a powerful sensor that accurately measures temperature, relative humidity, and carbon dioxide. For even more comprehensive monitoring, the SV23 adds AQI, TVOC, motion, vaping/smoking, noise, and PM 2.4. Finally, the SV25 includes the measures of the SV21 and SV23 plus light, formaldehyde, carbon monoxide, and barometric pressure readings.
The SV21 is best suited for meeting rooms and server rooms. The SV23 is ideal for monitoring in schools and enterprises. Lastly, the SV25 is perfect for health monitoring, specialty monitoring, and manufacturing facilities.
Video Intercom
Verkada’s TD52 Video Intercom is a cloud-native intercom that combines intuitive calling with enhanced perimeter security.
- 5MP camera with a wide 130° FoV lens for clear visitor views
- Clear audio with a 5W speaker and two omnidirectional MEMS microphones with noise suppression and acoustic echo cancellation
- Hybrid cloud architecture eliminates the need for NVRs/DVRs and fixed receiver stations
- IP66 and IK08 rated for deployment in direct sunlight, wet conditions or outdoor environments as cold a -40°F or as hot as 122°F
Learn more about the intercom’s flexible call receiving, dynamic smart call rotting, and scheduling here.
Desk Station
The Desk Station License unlocks the powerful features of Verkada’s Desk Station, an iPad-based application that simplifies entry requests and consolidates intercom actions and information into a single, intuitive interface. It is an ideal perimeter access control security solution.
- Full HD view of intercom calls
- Stream video and unlock doors
- View video intercom and security camera feeds
- Manage door access without elevated permissions
- Picture-in-picture capabilities for enhanced context
- Scalability with unlimited pairing of intercoms to Desk Station Application
- Easy configuration with drag-and-drop setup flow
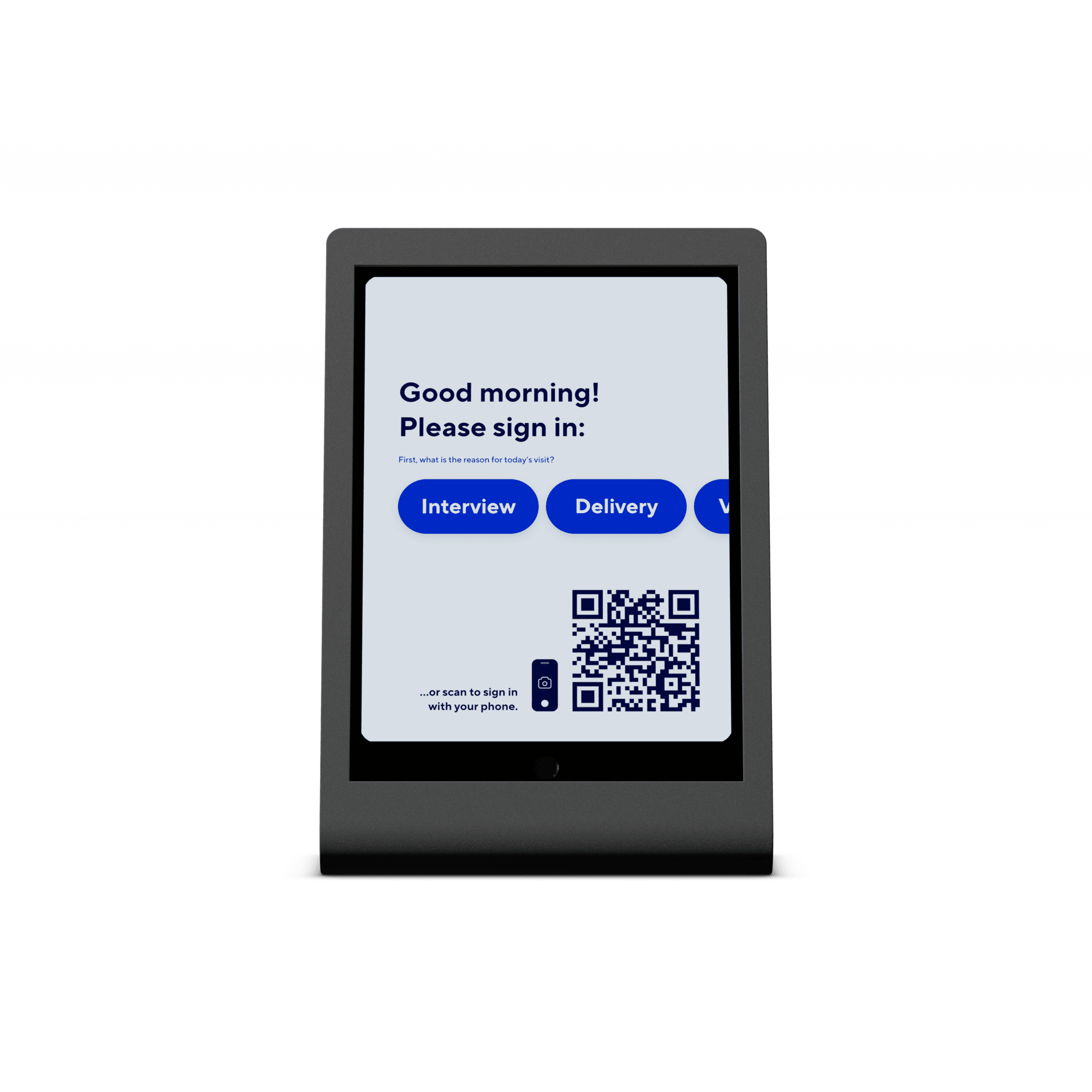
Verkada Guest
Verkada Guest is a native cloud-based solution that streamlines the check-in process for visitors. With the Verkada Guest security solution, admins can customize the check-in experience of their enterprise.
- Customizable Check-in: Tailored check-in experience makes visitors feel welcome and valued.
- Efficient Data Collection: Collect only necessary information, reducing wait times and streamlining the process.
- Digital Document Signing: Electronic document signing eliminates paper forms, enhancing efficiency and sustainability.
- Accurate Record-keeping: Capturing visitor photos ensures accurate record-keeping and improved security.
- Easy Identification: Customizable badges with color borders enable easy visitor identification.
- Optional Background Checks: Instantly screen visitors against US sex offender registries and run criminal background checks in real-time (via Checkr)
- Host Notifications: Automatic notifications to hosts via SMS, email, or Slack help manage visitor traffic and ensure a smooth experience.
- Touchless Check-in: Optional touchless sign-in via QR code or pre-registration with calendar invites for a seamless experience.
- Privacy: Expunge ID data of unflagged visitors immediately after check-in, and keeping flagged visitor data for a maximum of 90 days
Guest is the perfect perimeter security solution to simplify your administrative workflows. Contact our security experts here at Monarch to learn more!
Mailroom Management
Verkada’s Mailroom solution helps enterprises streamline mailroom operations and increase security through automated shipment tracking and camera integration.
- Automated scanning and shipment matching using OCR (optical character recognition) technology
- Easily match shipments to employees
- Instant notifications and reminders for employees when shipments arrive
- Employee self-service dashboard for shipment tracking and redirection
- Comprehensive reporting for office managers and receptionists
- Verkada camera integration for live and historical mailroom activity monitoring
- Ability to investigate lost shipments through camera footage filtering.

Mailroom License
Starting at $250.00 per month

Frequently Asked Questions — Perimeter Security Solutions
What are perimeter security solutions?
Perimeter security solutions refer to a combination of technologies, equipment, and strategies designed to protect the outer boundaries of a property. These solutions are implemented to detect, deter, and respond to unauthorized access and potential threats.
Why do I need perimeter security solutions?
Perimeter security solutions act as the first line of defense for your property. They help prevent unauthorized entry, monitor activities around the perimeter, and provide early detection of potential security breaches. These solutions are essential for enhancing overall security and ensuring the safety of your assets, employees, and visitors.
What are the key components of perimeter security solutions?
Perimeter security solutions encompass various components such as video surveillance cameras, access control systems, and more. These components work together to create a comprehensive security system that covers the outer boundaries of your property.
Can perimeter security solutions integrate with other security systems?
Yes, perimeter security solutions can integrate with other security systems such as access control systems. Integration enables seamless communication and coordination between different security components, enhancing overall effectiveness and response capabilities.
Are perimeter security solutions scalable?
Yes, perimeter security solutions can be tailored to the specific needs and size of your property. Whether you have a small business or a large enterprise, Monarch offers scalable solutions that can be customized and expanded as your security requirements evolve.
Keep Your Property Safe with Monarch’s Perimeter Security Solutions
Monarch’s perimeter security solutions offer the highest level of protection for your property. With advanced technologies and expert guidance, we ensure that your perimeter remains secure and your assets are safeguarded.
Our comprehensive approach combines video surveillance, access control, and more to create a robust security framework. Connect with our security experts at Monarch today to learn more about how our perimeter security solutions can provide peace of mind and enhance the safety of your property.