Your cart is empty.

Security Without Limits: Experience the Versatility of Serverless Solutions
Simpler, Smarter, Secure: The Future of Serverless Security
Without the need for expensive DVRS and NVRS or servers that require constant upkeep, serverless security systems are becoming increasingly popular. Verkada offers innovative, cloud-based cameras that eliminate the need for traditional servers, making security simple and scalable. With Verkada’s user-friendly and smart features, securing your premises has never been easier.
Say goodbye to complicated setups and hello to seamless, reliable security. Read on to learn more about Verkada’s serverless security solutions.
What is Serverless Security?
Serverless security, also known as cloud-based security systems, is a cutting-edge approach to securing your premises without the need for traditional servers, DVRS, or NVRS. With serverless security, the heavy lifting is done in the cloud, making it hassle-free and easy to manage.
Many people are opting for serverless security solutions as they provide numerous benefits. Serverless security allows for remote access 24/7, making it convenient and flexible for businesses and individuals alike. Say goodbye to complicated setups and hello to the future of security with serverless solutions!
Serverless Security vs DVRS/NVRS/Servers
Serverless security, such as the cloud-based solutions offered by Verkada, provides numerous advantages over traditional security systems with DVRS/NVRS/servers. Here are some key reasons why serverless security is the better choice:
Simplified Setup and Management
With serverless security, there is no need for complicated servers or DVRS/NVRS. The system operates in the cloud, making it easy to set up and manage. This eliminates the need for on-site hardware, reducing installation and maintenance costs, and minimizing potential points of failure.
Scalability and Flexibility
Serverless security solutions like Verkada offered by Monarch are highly scalable, allowing for unlimited storage on the camera and in the cloud, and unlimited users. This makes it convenient for businesses of all sizes to expand or adjust their security needs as required. Additionally, serverless security enables remote access 24/7, providing flexibility and convenience for monitoring and managing security remotely.
Advanced Features and Analytics
Serverless security leverages advanced features such as AI-based video analytics, smart filters, and live alerts. These tools provide enhanced security capabilities, such as real-time alerts for suspicious activities, intelligent search and filtering, and shareable live feeds. This allows for proactive monitoring and efficient management of security events.
Reliable and Future-Proof
Serverless security systems are designed for reliability and durability, with solid-state storage (SSD) technology and regular automatic software updates to ensure optimal performance. Additionally, serverless security is future-proof, as it can adapt to evolving security needs and technological advancements without requiring costly hardware upgrades.
Trust Monarch and Verkada serverless security solutions to provide efficient, user-friendly, and enterprise-grade security for your premises.
Why Choose Verkada?
Verkada’s serverless security solutions stand out from traditional security systems because they are designed to be user-friendly, scalable, and flexible all while providing enterprise-grade security.
User-Friendly
- Solid-state Storage (SSD)
- Simple Plug-and-Play Install
- Time lapse
- Floor Plan
- Regular, Automatic Software Updates
- Remote Access 24/7
Limitlessly Smart
- AI-Based Video Analytics
- Smart Filters
- Live Alerts
- Shareable Live Feeds
- 10-Year Warranty
Scalable
- Unlimited Storage on Camera and Cloud
- Unlimited Users Allowed
- Infinitely Scalable
Severless Security Camera Systems
Monarch offers cutting-edge serverless security solutions to safeguard your property without relying on servers or traditional security systems. With state-of-the-art technology, continuous monitoring, and rapid response capabilities, Verkada security systems are designed to protect your business or organization against threats.
Whether you own a retail store, restaurant, commercial building, manufacturing facility, school, or healthcare facility, Monarch has the right serverless security solution for you. Contact us today to learn more and secure your property with our innovative serverless security technology.
The Dome Series for Serverless Security
The Dome Series from Verkada provides enterprise-grade security in a variety of models suitable for any industrial environment – indoors or outdoors. These IP security cameras with analytics have a long-lasting, vandal-resistant design and sensor resolutions of up to 4K.
Design
- Durable, vandal-proof housing with outdoor models having a weather-resistant design
- Indoor models: IK08 impact rating
- Outdoor models: IK10 impact and IP67 weather ratings
Functionality and Storage
- High resolution cameras — 5MP or 4k
- 4k available only on CD62 & CD62-E
- Max of 365 days of footage storage in standard quality
- 128GB – 2TB of onboard storage
- Equipped with audio
- Low–bandwidth impact
Features
- Edge processing for motion, People, and Vehicle Analytics
- Occupancy Trends available only on Dome Series cameras
- Zoom capabilities – both optical and digitally
- CD42, CD42-E: Fixed, with 3x Zoom Digitally
- Other models: Zoom, with 3x Optical and Digital Zoom
- IR Range
- 15m (CD42, CD42-E)
- 30m (CD52, CD52-E, CD62, CD62-E)
The Bullet Series for Serverless Security
The Bullet Series from Verkada is built to withstand extreme conditions, and its conspicuous appearance is meant to deter would-be assailants. Essentially, it is the ideal cloud-based industrial security camera for harsher areas.
Design
- Durable and weather-proof
- IP67 weather rating and IK10 impact rating
- Lens – Choose between wide-angle or telephoto
Functionality and Storage
- High resolution cameras – up to 4k
- 4k available only with CB62-E and CB62-TE
- Max of 365 days of footage retention in standard quality
- 265GB–2TB of onboard storage
- Low–bandwidth impact
Features
- License Plate Recognition available only for telephoto cameras
- Edge-based processing for motion, people and vehicle analytics
- NDAA compliant
- Zoom capabilities
- CB52-E, CB62-E: Zoom, with up to 3x Optical and Digital zoom
- CB52-TE, CB62-TE: Telephoto Zoom, with 8-20mm focal length
- IR Range
- CB52-E, CB62-E: 30M
- CB52-TE, CB62-TE: 50M
The Mini Series for Severless Security
Verkada’s mini series offers a compact and discreet security solution. These cameras are designed to be small and unobtrusive, making them well-suited for installation in tight spaces or in areas where a larger camera may be noticeable.
Design
- Small and discreet camera with 5MP resolution
Functionality and Storage
- Max of 365 days of footage retention in standard quality
- 128GB – 2TB of onboard storage
- Low band-width impact
Features
- Edge–based processing for motion and tamper detection along with People Analytics
- Fixed, with up to 3x Digital Zoom
- Audio available only on CM41 and CM41-E
- IR Range: 15m for CM41 and CM41-E
- N/A for CM41-S
The Fisheye Series for Serverless Security
Verkada’s fisheye industrial security camera offers dynamic viewing experiences with sophisticated onboard processing and a wide–angle 12MP image sensor. In fact, there are five different viewing options available to users: panoramic, digital pan-tilt-zoom, 2-way split, 3-way split, and 4-way split.
Design
- Durable and weatherproof
- IP67 weather rating and IK10 impact rating
- 12MP image sensor for wide–angle coverage
Functionality and Storage
- Max of 90 days of footage retention in standard quality
- 512GB–2TB of onboard storage
- Low–bandwidth impact
- 180 degree field of view
Features
- Five viewing modes
- Nighttime visibility with IR illuminators (20m/66ft)
- NDAA
- Equipped with audio
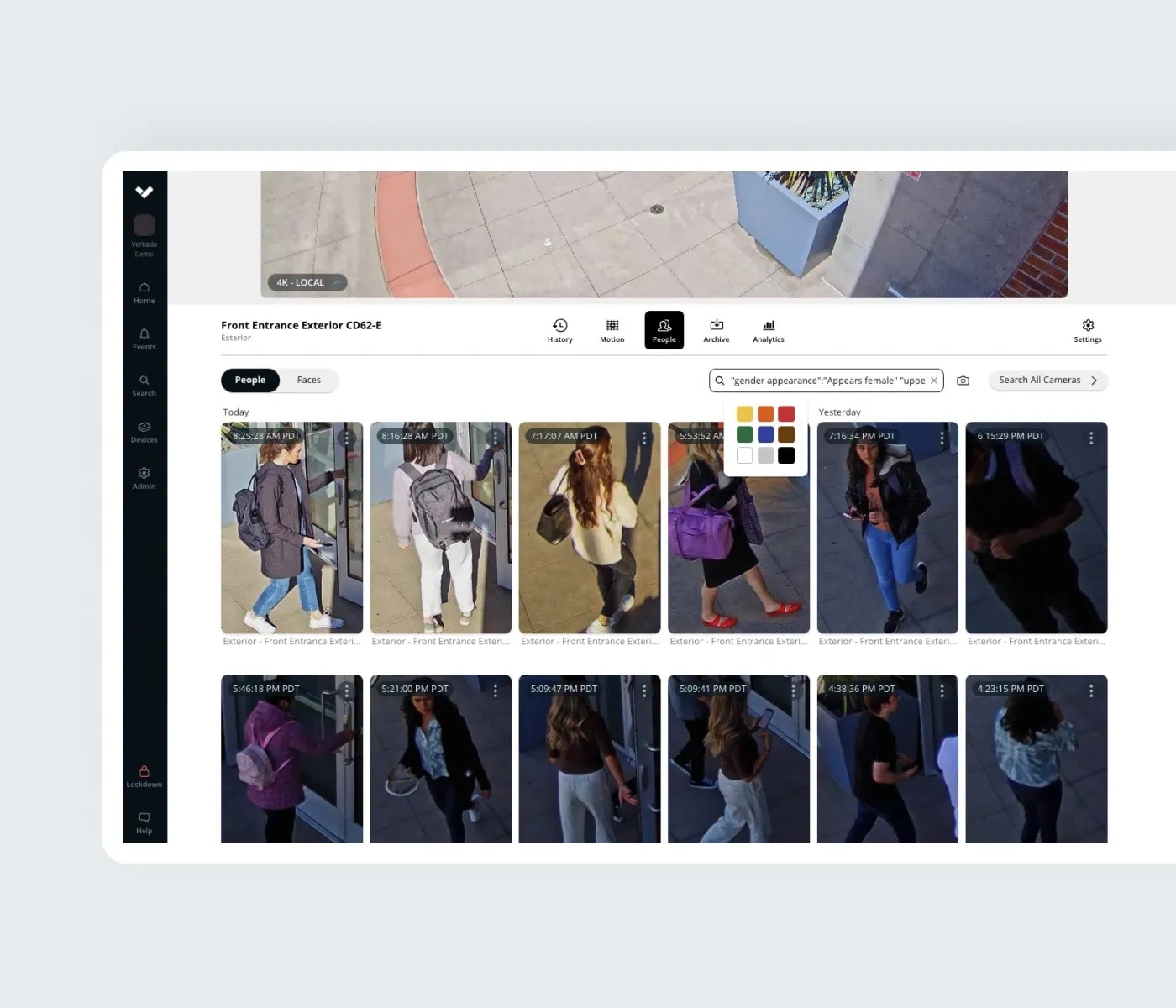
People Analytics — Serverless Security Cameras
People Analytics combines cloud-based computer vision with intelligent edge-based video processing to give users high-quality images of every person recognized in the scene.
- Face Search*
- You can quickly find people who look like a face you already have in your organization. You can also upload an image of a face of a person of interest.
- Occupancy Trends
- Estimate the number of people who cross a customizable digital line on a video feed.
- Keep track of how a space is being used in order to improve business operations.
- Person History
- Search through high-resolution snapshots of people detected in the frame.
- Save screenshots or easily access associated high-resolution video.
- Examine Anywhere
- People Analytics is accessible from any device and from virtually any location in the world.
- Filters for Attributes
- Filter by a variety of criteria, such as clothing color, gender appearance, and facial matches.
- Cross Camera Tracking
- Quickly identify people of interest or potential suspects across all cameras at all sites.
- Record and export multiple angles of a person to provide evidence quickly.
*It is important to use the face recognition technology ethically, respecting individuals’ rights to privacy and avoiding bias.

Frequently Asked Questions — Serverless Security
What is serverless security?
Serverless security refers to a type of security system that does not rely on traditional servers, DVRS, or NVRS to operate. Instead, it utilizes cloud-based cameras and cutting-edge technology to provide advanced security solutions.
How do Verkada cloud-based cameras work?
Verkada cloud-based cameras capture and transmit video footage to the cloud, where it is securely stored and accessible remotely. These cameras also offer onboard storage. This eliminates the need for on-site servers or DVRs, providing a more scalable and flexible security solution.
Are Verkada cloud-based cameras secure?
Yes, Verkada takes security seriously. Their cloud-based cameras utilize end-to-end encryption, regular security updates, and robust authentication measures to protect against unauthorized access and ensure data privacy.
How easy is it to install Verkada cloud-based cameras?
Installing Verkada cloud-based cameras is simple and straightforward. They are designed for easy deployment and can be set up by following the provided installation guides. No complex wiring or additional servers are required since they are serverless secuirty cameras.
Can I access the video footage from Verkada cloud-based cameras remotely?
Yes, you can access the video footage from Verkada cloud-based cameras remotely. You can view the live feed and recorded footage from anywhere using the Verkada mobile app or a web browser, allowing you to monitor your premises even when you’re not on-site.
What happens to the video footage captured by Verkada cloud-based cameras?
The video footage captured by Verkada cloud-based cameras is securely stored both in the cloud and onboard the camera. It is encrypted and protected against unauthorized access, ensuring the privacy and security of your data.
Do Verkada cloud-based cameras have advanced features for enhanced security?
Yes, Verkada cloud-based cameras come with advanced features like intelligent video analytics, which can detect and alert for events such as motion, tampering, and facial recognition. These features provide an added layer of security to your surveillance system.
Unlocking New Possibilities: Embrace the Future of Serverless Security
Monarch’s serverless security solutions, powered by Verkada’s innovative cloud-based cameras, provide advanced security without relying on servers, DVRS, or NVRS. With cutting-edge technology, continuous monitoring, and rapid response capabilities, Verkada’s serverless security systems offer robust protection against threats for businesses and organizations of all types.
Say goodbye to traditional security systems and embrace the future of serverless security with Monarch. Contact us today to learn more and secure your property with Verkada’s state-of-the-art serverless security solutions.