Your cart is empty.

The Future of Security with Access Control Technologies
Experience the Next Level of Security with Access Control Technologies
At Monarch, we are dedicated to providing state-of-the-art solutions that safeguard your business. Access control technologies offer a wide array of features, from keycards to biometric scanners.
Discover how access control technologies can streamline your operations, enhance security, and provide you with peace of mind. Connect with our security experts here at Monarch to learn more.
Unveiling the Power of Cloud-Based Access Control Technologies
Embracing the latest advancements in technology, Verkada’s cloud-based access control systems offer unparalleled flexibility, scalability, and convenience. Say goodbye to traditional physical keys and cumbersome on-premise servers.
With cloud-based access control, you can manage access permissions remotely, granting or revoking access with just a few clicks. Verkada’s integrated platform allows for seamless integration with other security systems, enhancing overall protection. Whether you’re a small business or a large enterprise, Verkada’s cloud-based access control solutions adapt to your needs, providing robust security and peace of mind.

Explore the Benefits of Access Control Technologies
Access control technologies have revolutionized security measures across industries, providing a robust solution to safeguard physical spaces and digital assets. Consider the following benefits:
- Enhanced Security: Access control systems provide a secure and controlled environment by regulating entry and restricting unauthorized access.
- Cost-Effective: Automated access control reduces the need for physical keys and manual monitoring, leading to cost savings over time.
- Enhanced Productivity: Access control streamlines the entry process, eliminating the need for manual verification and enhancing operational efficiency.
- Instant Alerts and Notifications: Real-time alerts are triggered for any security breaches or attempted unauthorized access, allowing quick response and mitigating potential risks.
Verkada’s access control technologies offer a wide array of benefits, making them an essential component of any comprehensive security strategy.
Empowering Industries with Tailored Access Control Solutions
In today’s ever-evolving security landscape, access control technologies have become an integral part of various industries, safeguarding people, assets, and sensitive information. Verkada’s access control solutions cater to a diverse range of sectors, providing tailored security measures that meet their specific needs. Consider the following:
- Education: Safeguarding students and faculty while maintaining a conducive learning environment.
- Healthcare: Ensuring patient privacy and protecting critical medical equipment and supplies.
- Retail: Preventing unauthorized access and reducing inventory shrinkage.
- Government: Protecting government facilities and confidential information.
- Finance: Securing financial institutions and sensitive financial data.
- Manufacturing: Controlling access to production areas and protecting intellectual property.

Frequently Asked Questions – Access Control Technologies
What is an access control system?
Access control technology refers to the methods and devices used to regulate access to physical spaces or digital resources. It allows authorized individuals to enter specific areas or use designated resources while keeping unauthorized individuals out.
Is data privacy ensured with Verkada’s access control solutions?
Yes, Monarch prioritizes data privacy and security. Our access control technologies adhere to industry standards and utilize encryption protocols to protect sensitive information.
How user-friendly is Verkada’s access control system?
Verkada’s access control technologies are designed with user experience in mind. The intuitive interfaces and straightforward setup ensure ease of use for both administrators and end-users.
Why Choose Verkada?
Verkada’s access control technologies stand out from traditional security systems because they are designed to be user-friendly, scalable, and flexible.
User-Friendly
- Solid-state Storage (SSD)
- Simple Plug-and-Play Install
- Time lapse
- Floor Plan
- Regular, Automatic Software Updates
- Remote Access 24/7
Limitlessly Smart
- AI-Based Video Analytics
- Smart Filters
- Live Alerts
- Shareable Live Feeds
- 10-Year Warranty
Scalable
- Unlimited Storage on Camera and Cloud
- Unlimited Users Allowed
- Infinitely Scalable
Access Control Technologies: How it Works
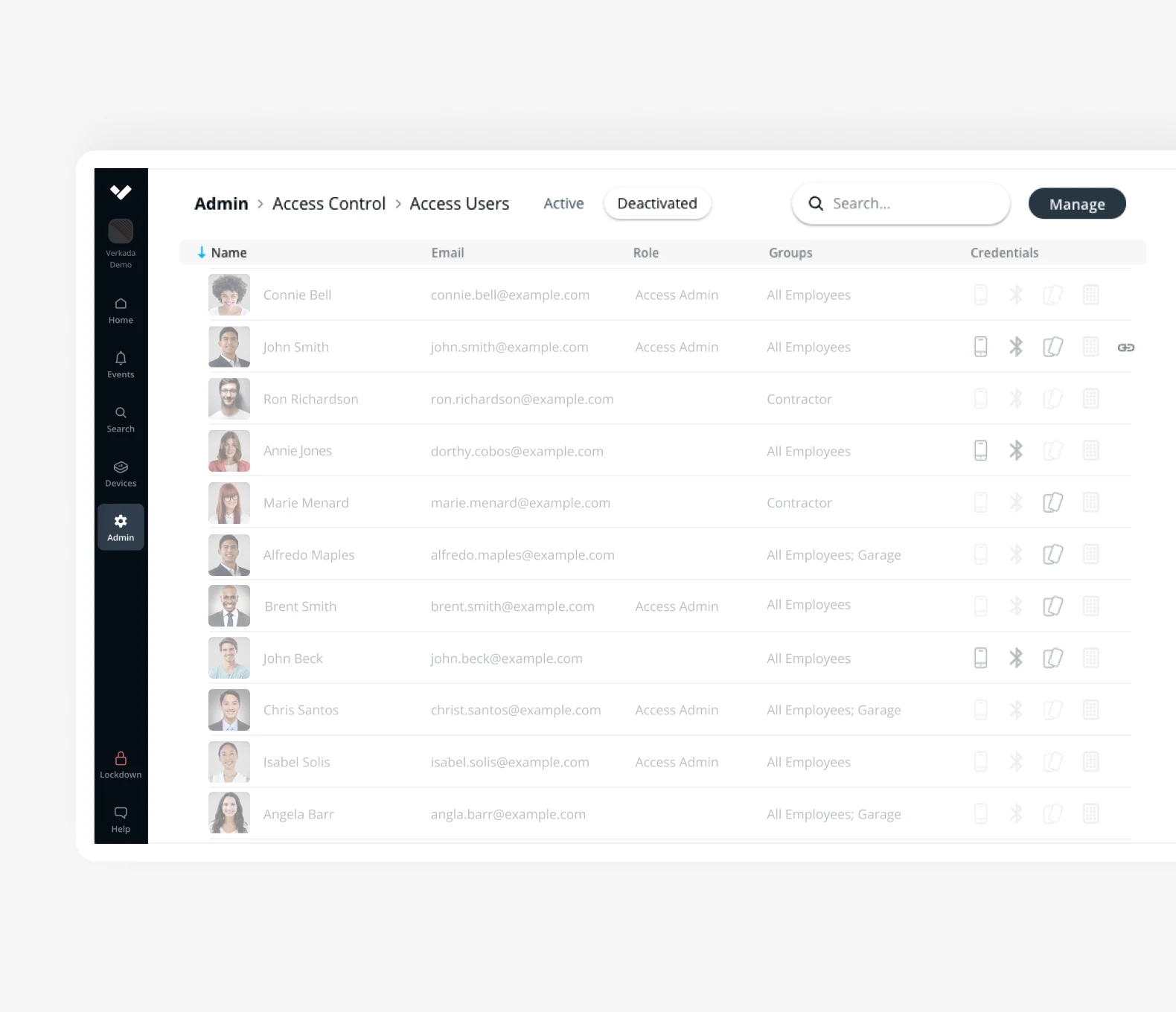
You can manage access control on the Verkada Command platform which is where you can access and monitor all of your devices.
- Specify the user groups or access levels of the facility on Verkada Command.
- Design badge templates for each user group or access level
- Print the badges and issue credentials either in bulk or individually
Command Features
- Integration with Video Surveillance: Connect with Verkada cameras for real-time video analytics on access events
- Synchronize Profiles: Synchronize users from SSO systems such as Okta and Azure Active Directory, and natively capture access levels and groups. Used for automatic employee configuration, onboarding, and offboarding.
- Provisioning with a Single Click: With a single click, employees or students can be issued bluetooth credentials or a physical ID card.
- Customizable Access Levels and Schedules: Allows for tailored access control based on employee roles and schedules.
- Log of Badge Events: Access a log of badge events to ensure that only authorized individuals have access to secure areas.
- Unlock Doors from Anywhere, Anytime: Users can remotely unlock authorized doors using either the Verkada Pass and Command Mobile apps
- One-Tap Instant Lockdown: Create custom Lockdown scenarios that can be activated with a single tap to immediately secure buildings in the event of an emergency.
Verkada’s Access Control Technologies
Verkada’s access control technologies provide robust security features designed to enhance safety for businesses. These access control systems offer advanced features such as keyless entry, remote management, and real-time activity tracking, providing a secure and efficient solution for your security needs.

Door Controller AC41
Priced at $1799

AD32 Multi Format Card Reader
Priced at $349

AX11 IO Controller
Starting at $216.50 per month
The Verkada AC41 Door Controller
This door controller is a powerful and easy-to-use access control technology that combines enterprise-grade security with a cloud-based management platform.
- Easily manage doors and access across your organization on the Command platform (schedules, users, building access)
- Supports secure touchless access using Bluetooth and Verkada’s Pass app
- Works with existing door hardware and readers
- 10-year warranty on all hardware

The Verkada AD32 Door Reader
This Verkada door reader is a versatile and robust access control device that allows individuals to enter doors using low and high-frequency cards or a mobile device with the Verkada Pass app. Consider the following attributes of the Door Reader access control technology:
- Can withstand a harsh environment – IP65 and IK08 ratings
- Controlled through the Command platform
- Two different options:
- Mullion Mount Plate: This option has a sleek design and can be used in smaller spaces such as door frames.
- Single Gang Mount Plate: This is a common card reader format that can replace existing reader mounts or be used on traditional installations.

The Verkada AC62 16 Door Controller
The AC62 16 Door Controller is an enterprise-grade access control panel that simplifies access control for up to 16 doors. It offers the scale and simplicity of the cloud, making access control more efficient and effective.
- Seamless integration with Verkada or third-party readers, REX devices, AUX inputs, and wet or dry lock configurations.
- Connection to the Fire Alarm Interface for emergency events.
With easy installation and integration with existing door hardware, the AC62 is a top choice for any organization seeking to enhance their security measures.
The Verkada AX11 IO Controller
The AX11 IO Controller from Verkada is a versatile and scalable device that enables customers to integrate more inputs and outputs to their existing access control systems. With 16 inputs and 16 outputs, customers can easily integrate access control, cameras, sensors, and alarms.
Simple, Scalable, and Flexible Access Control
- Event Bridge technology: This feature allows you to bring door events with video analytics into the Command platform while using your existing access control or alarm system. Also provides real-time alerts and reports
- Supports third-party card door readers: The AX11 IO controller works with Verkada and third-party card door readers, offering you the flexibility to choose the best access control solution for your business.
- Elevator access control: Manage access to different floors of your building with a Verkada or Wiegand reader.
An Overview of Verkada’s Access Control Technologies
Monarch offers Verkada’s wireless access control technologies. Consider the key features that make Verkada’s systems stand out:
- Centralized Management: Access and manage your access control system from anywhere with a cloud-based platform that is easy-to-use, simplifying administration and oversight.
- Real-Time Alerts: Receive SMS and email alerts for doors held open, suspicious entry, and emergency scenarios, allowing for immediate response and threat mitigation.
- Mobile Access: Enjoy the convenience of mobile credentials, enabling authorized individuals to access secured areas using their smartphones.
- Touchless Solutions: Embrace touchless access options, reducing physical contact and addressing hygiene concerns.
- Visitor Management Integration: Efficiently manage visitor access and streamline registration processes by integrating visitor management functionalities.
- Robust Security: Benefit from robust security measures, including encryption, multi-factor authentication, and audit trails, to protect your premises.
Experience the future of access control technologies with Monarch.
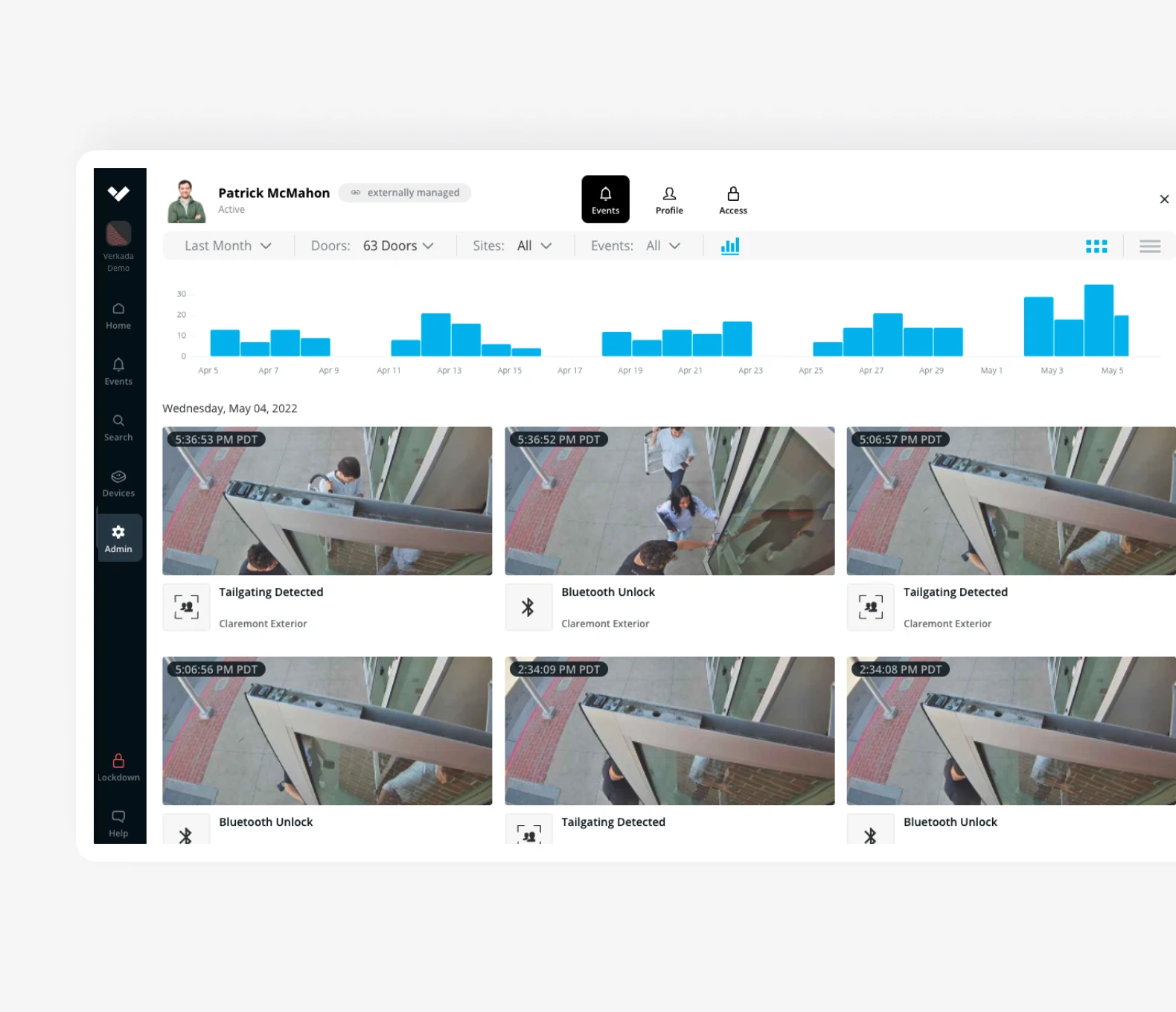
Verkada’s Access Control Systems: Video Integration
With Verkada’s video integration, businesses can achieve enhanced security, proactive incident response, and comprehensive monitoring of their access control systems.
- Visual Verification: Associate Verkada cameras with access-controlled doors to provide visual verification of access events, improving security measures.
- Comprehensive Monitoring: Add multiple cameras to capture events from multiple angles, providing comprehensive coverage and situational awareness.
- Incident Investigation: Quickly export video evidence for investigations, facilitating incident analysis and ensuring a proactive response.
- AI-Powered Analytics: Leverage Verkada’s advanced video analytics capabilities, such as crowd detection and person of interest recognition, to enhance security beyond physical access control.
- Lockdown Capabilities: Trigger instant lockdowns on doors and sites from Verkada Command web or mobile, enhancing emergency preparedness and response.
Partner with Monarch to implement these access control technologies and elevate the protection of your business.
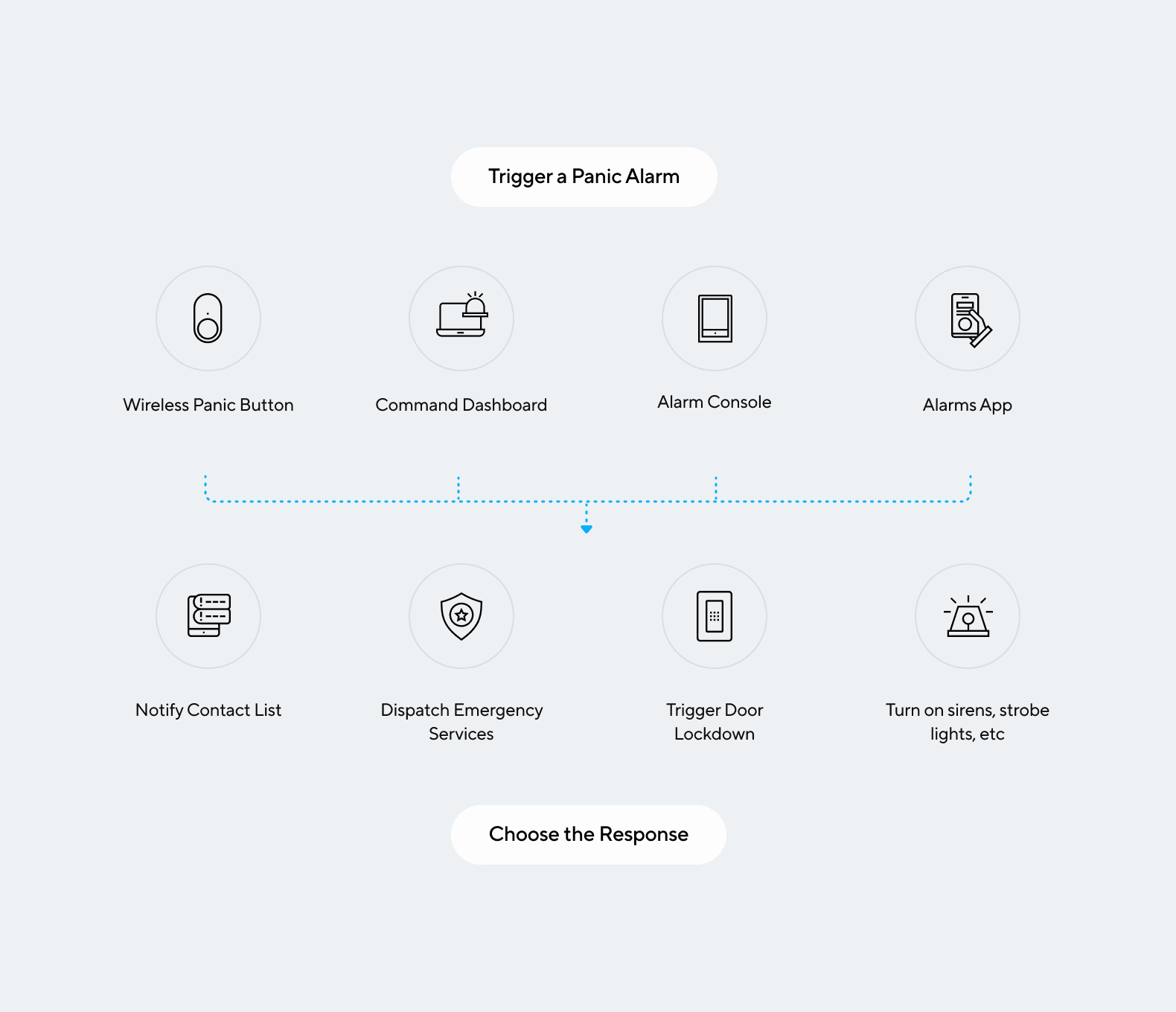
The Lockdown Feature
The lockdown feature ensures swift response and emergency preparedness by automating lockdown procedures. Here’s why the Verkada lockdown feature is crucial for access control systems:
- Instant Response: Activate lockdown scenarios with a single click, ensuring immediate response to emergency situations.
- Customizable Scenarios: Create lockdown scenarios at various levels—doors, sites, buildings, or the entire organization—to suit your specific security needs.
- Automated Alerts: Configure notifications and alerts for lockdown scenarios, ensuring the right personnel are informed promptly.
- Multi-Device Activation: Trigger lockdowns from Verkada Command, Verkada Pass App, an alarm event, or a dedicated panic button, providing flexibility and quick response options.
- Emergency Response Workflows: Integrate Verkada Alarms to streamline emergency response by calling authorities or activating other response protocols during a lockdown.
- Enhanced Safety: Roll call reports allow for quickly identifying who is safe and who may be missing during emergency scenarios.
Experience the peace of mind that comes with advanced access control systems tailored to your specific security requirements.
Secure Your World with Verkada’s Access Control Technologies
Monarch offers cutting-edge access control technologies that empower businesses and organizations to create secure environments tailored to their unique needs. From cloud-based solutions to advanced video analytics, our products provide seamless integration and user-friendly interfaces.
With a focus on innovation, reliability, and data privacy, Verkada’s access control systems ensure peace of mind for all stakeholders. Whether it’s safeguarding educational institutions, healthcare facilities, or corporate offices, our solutions enable effective access management, preventing unauthorized entry and protecting critical assets. Embrace the future of security with Monarch and take control of your organization’s safety and success.